2015 Все новости технологии ССЛ
18/12/2015 Symantec: Certificate Transparency for OV and DV Products
Certificate Transparency helps to guard against several certificate-based threats such as mis-issued certificates and maliciously acquired certificates. Symantec initially rolled out CT support for all brands of our EV products in December last year and is expanding CT support across all our brands of OV products in January 2016 and all brands of DV products in February 2016.
18/12/2015 Symantec: new chain cert for DV certs
Symantec will be introducing new intermediate certificates for the RapidSSL, RapidSSL Wildcard, QuickSSL and QuickSSL Premium products. We will provide links to these new intermediate certificates in our Knowledgebase after GA in early 2016.
18/12/2015 Symantec has Discontinued the Safe Site Product
As of December 1st, Symantec has discontinued selling the Safe Site product. If you have an active Safe Site product, it will still work throughout the remainder of its life; however, the malware scanning feature will no longer work. We apologize for any inconvenience this may cause.
18/12/2015 Google Will Restrict Relocation to HTTPS Sites
Google has clear intentions to create a more secure Web. One of their campaigns to do so is nicknamed "Powerful Features", and defines a set of browser features that can only be used over HTTPS because the data they provide is so sensitive. Google has just announced that Geolocation - an API which allows you to retrieve the geographical location of the user - will soon be restricted to HTTPS as part of the Powerful Features plan.
15/12/2015 adgrafics
Основные события безопасности в инет 2015 от Bruce Morton (Entrust)>>>
14/12/2015 adgrafics
Some major browsers have already started while others plan to start displaying security warnings or even block sites that use SHA-1 certificates in 2016. Furthermore, international cryptography researchers recently warned of a significantly increased risk in using SHA-1 certificates and recommend migration to SHA-256 certificates as soon as possible Make sure you replace their SHA-1 certificates with SHA-256 certificates to eliminate the security risk associated with SHA-1 certificates.
13/12/2015 Ballot 118 – SHA-1 Sunset (passed)
Voting on Ballot 118 – SHA-1 Sunset closed on 16 October 2014. The Chair received “yes” votes from Actalis, ANF, Buypass, Certinomis, Chunghwa Telecom, Comodo, DigiCert, Disig, Entrust, GlobalSign, GoDaddy, Google, Izenpe, Kamu Sertifikasyon Merkezi, Logius PKIoverheid, Microsoft, Mozilla, Opentrust, Opera, QuoVadis, SSC, StartCom, Symantec, Trend Micro, TURKTRUST, TWCA, and WoSign. SECOM Trust Systems voted no. There were no abstentions. Therefore, Ballot 118 passed >>>
10/12/2015 Quarterly SSL Industry Snapshot
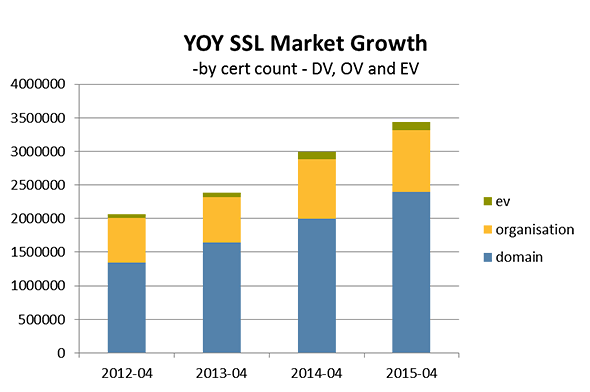
The October 2015 Netcraft report found 3,682,148 valid SSL certificates, with a monthly gain of 19,862 (+ 0.54% growth). New certificates totaled 107,695 across all CA’s in October. For October 2014 vs. October 2015 the total SSL market grew 13%
10/12/2015 adgrafics
Researchers Urge SHA-1 To Be Retracted Earlier Than Planned New research shows that the SHA-1 internet security standard can in fact be retracted sooner than originally planned. An international team of cryptanalysts have discovered that the cost of breaking SHA-1 is significantly less than previously thought – and are now urging the industry to respond. SHA-1 is the industry standard for digital signatures which secure credit card transactions, electronic banking and software distribution. Currently, the plan is to move to an SHA-2 signature by January 2017, after which all SHA-1 signatures will be marked as ‘insecure’. However, the cryptanalysts – Marc Stevens, Pierre Karpman and Thomas Peyrin – now estimate that false SHA-1 signatures will be possible to make much sooner than this date.
09/12/2015 CA/B Forum: New EU Law For Qualified Web Server TLS Certificates
October’s CA/B Forum face-to-face meeting took place in Istanbul, Turkey – and more than 40 global organizations attended. Symantec’s Dean Coclin chaired the event, during which Andrea Servida from the EU Commission spoke about the new EU law for Qualified Web Server TLS Certificates. These certificates will be issued by Qualified Certificate Authorities in Europe. However, as organizations are not required to use them and they will not affect the display of any web browser, it remains to be seen whether they will prove successful. Time will tell Website authentication services under eIDAS Regulation
09/12/2015 Symantec
fTLD Registry Services partners with Symantec to provide verification services for all .BANK generic top-level domains.
This is an essential part of the increased security required to ensure greater trust online between banks and their customers.
Download our whitepaper and supporting resources>>>
09/12/2015 Symantec
Happy Holidays And A Prosperous New Year
Dear Valued Business Partners
As we come to the close of 2015, I want to personally thank you for another incredible year and would like to send my sincere gratitude for your loyalty and partnership.
Symantec's Partners are the heart of our business and in 2016 we will continue to provide the most robust security solutions and partner support in the market. In 2015 we added even more value to partners including, Ready Issuance, Online Verification for OV, SMS Text Notification Service, Website Security Developer Portal, CyptoExec, new wildcard offerings and ECC/RSA Hybrid certificates and next year we are planning to go even bigger. It has never been more exciting and rewarding time to be a business partner with us.
As 2016 approaches we will continue to work tirelessly to ensure your success. On behalf of the entire team here at Symantec, thank you once again for your loyalty and your partnership.
Best wishes for peace and joy this holiday season and a New Year of health, happiness and prosperity,
Philip Antoniadis
Sr. Director, Global Sales
Symantec Website Security Solutions
01/12/2015 adgrafics
Ходят слухи что CabForum ужесточит требования по выпуску CodeSign сертификатов. Целью является физически вынуть ключ из компьютера и сделать его более трудным для кражи. Правила SSL >>>
24/11/2015 Public Statement Regarding Pearson Credential Manager System
We recently were made aware that an unauthorized third party placed malware on Pearson VUE’s Credential Manager System—which is used by adult learners to support professional certifications and licenses. The unauthorized third party improperly accessed certain information related to a limited set of our users. We have been updating affected customers and will continue to do so. We have also set up a dedicated hotline to assist users with any questions or concerns they may have: (855) 270-9182 or +1 (512) 201-2203 for international users.
Please see our Frequently Asked Questions (FAQs) for more information
19/11/2015 Updated Firefox Security Indicators
Over the past few months, Mozilla has been improving the user experience of our privacy and security features in Firefox. One specific initiative has focused on the feedback shown in our address bar around a site’s security. The major changes are highlighted
19/11/2015 IPv6 for OCSP and CRL
Since 26th October 2015, Symantec have been migrating OCSP and CRL services from Akamai IPv4 network to Akamai dual-stack IPv4+IPv6 network. This migration was completed earlier this month, and there will be no service disruption for our end-customers. There will be no changes for IPv4 customers. They will continue to hit the same IPv4 IP addresses for OCSP and CRL services. For dual-stack customers, OCSP and CRL services will be available on IPv6 addresses instead of IPv4 addresses.
19/11/2015 SGC Super Cert End of Life Phase 2/Midterm Upgrade
Since July 2015, Symantec no longer sells Thawte’s SGC SuperCert products. Customers still using Thawte’s SGC SuperCert product can migrate to an alternative product such as Thawte SSL Web Server with EV via Symantec’s midterm upgrade capability
19/11/2015 SAN Limit Increase for Symantec and Thawte
Symantec is increasing the number of SANs per certificate from 24 to 100 for all our Thawte and Symantec products that support SAN. This will give our Thawte and Symantec customers more flexibility when it comes to securing multiple domains. Geotrust certificates already support up to 100 SANs today. These changes will be available in December 2015.
19/11/2015 Certificate Transparency for OV and DV Symantec certs
Symantec is one of a few organizations to operate multiple public CT log servers. Symantec initially rolled out CT support for all brands of our EV products in December last year and is expanding CT support across all our brands of OV products in January 2016 and all brands of DV products in February 2016.
19/11/2015 Certificate Transparency for OV and DV Symantec certs
Symantec will be introducing new intermediate certificates for the RapidSSL, RapidSSL Wildcard, QuickSSL Premium, QuickSSL
Symantec is targeting to make the new intermediate certificate authorities available in early December
05/11/2015 CA/B Forum Istanbul 2015
2015-10-07 Face-to-Face Meeting Minutes – Meeting 36 Istanbul >>>
While some face to face meetings can be rather mundane and boring, that can’t be said about October’s CA/B Forum meeting in Istanbul, Turkey. Guest speaker Andrea Servida from the European Commission gave an overview of the new eIDAS regulation on electronic identification and trust services. While not everyone in the room agreed with his points, all were made aware that this has now become the law in the EU and certificate authorities which plan to issue the new EU Qualified website certificates must comply with it. Unfortunately, the law appears to make it a requirement that the Certificate Authority (or Trust Service Provider-TSP as spelled out in the regulation) must be based in the EU or in a country that has an agreement with the EU. This could limit CA choices for EU website owners to only smaller CAs located in the EU, and potentially drive up certificate prices. Mr. Servida’s presentation
02/11/2015 Symantec
In September 2015, we reported that a small number of test certificates for Symantec’s internal product testing had been issued for domains that we did not own, in violation of our stated policies. We have found others, most of which were for non-existent and unregistered domains, and we intend to continue with being transparent in updates regarding what we have found and the steps that we have taken to ensure that similar internal policy violations do not occur again. It is important to note that throughout this investigation, we have uncovered no evidence of malicious intent, nor any harm to users, organizations, or anyone in the ecosystem. Further, we have reconfirmed that all of these test certificates have all been revoked and/or have expired and we have worked directly with the browser community to have them blacklisted as an extra precaution. Nonetheless, Symantec takes this incident extremely seriously, as this type of product testing was not consistent with the policies and standards we are committed to uphold.
23/10/2015 OTA
Recognizing a need for privacy and security best practices for the growing number of consumer IoT devices, the OTA established the IoT Working Group in January which recently released a draft Internet of Things Trust Framework. Ahead of the formal release on November 18th, the OTA will discuss these guidelines for IoT manufacturers, developers and retailers to follow when designing, creating, adapting and marketing connected devices in two key categories: home automation and consumer health and fitness wearables.
08/10/2015 Quarterly SSL industry snapshot
The July 2015 Netcraft report found 3,606,431 valid SSL certificates, with a monthly gain of 94,970 (+ 2.70% growth) - the largest monthly gain since January.
For July 2014 vs. July 2015:
- The total SSL market grew 14%
- Total EV units grew by 20%
- Total OV units grew by 7%
- Total DV units grew by 17%
07/10/2015 Deciphering Chrome’s security warnings
Many people have been confused by the security warnings that Google added to Chrome in the last few releases. Here’s a Google site >>> that provides a clear explanation of what conditions generate each message. At the last CA/Browser Forum face-to-face meeting, Google reiterated that they’re doing a lot of work in this space, and they’ve realized that the current messaging is more appropriate for a technical audience but not for the general public. They intend to continue evolving their security user interface to provide appropriate messages for different audiences.
05/10/2015 Introducing Symantec ECC 256: 64,000x more secure than RSA 2048
Symantec Elliptic Curve Cryptography (ECC) certificates set new standards for online protection, by enabling much stronger security with a far shorter algorithm key. ECC 256 is 64,000 times more secure than RSA 2048 - despite being nearly 10 times shorter. This means your customer can load websites faster and enjoy more fluent server functionality while staying comprehensively safe.
04/10/2015 Symantec customer alert !
We want to bring to your attention three separate issues that require you to replace and revoke SSL certificates. Below is a description of each issue followed by a list of affected SSL certificates
- Due to the way the maximum validity of an SSL certificate (number of days instead of actual months) is calculated, a small portion of Symantec, GeoTrust and Thawte customers obtained Extended Validation (EV) SSL certificates with a maximum validity that appear to be beyond the Certification Authority/Browser Forum mandated 27-month period. Certificates with a validity period beyond this limit are causing a warning message within the Chrome browser, versions 42 and above. These SSL certificates need to be replaced with a certificate with a validity period under 27 months before 26 October 2015. Replacement SSL certificates are always offered at no additional cost.
- A bug was discovered that enabled a small portion of Symantec, GeoTrust and Thawte customers to buy Extended Validation (EV) SSL certificates with blank Business Category or Registration Number fields. These SSL certificates need to be replaced with a certificate with completed Business Category or Registration Number fields before 26 October 2015. Replacement SSL certificates are always offered at no additional cost.
- A bug was also discovered that allowed customers to add internal names and reserved IP addresses in the Subject Alternative Name (SAN) extension or Subject Common Name field of an SSL certificate. Formerly permissible, SSL certificates chained to public roots, that expire after 1 November 2015, cannot contain internal names or reserved IP addresses. These SSL certificates need to be replaced with a certificate with a compliant FQDN or non-reserved IP address before 26 October 2015. Replacement SSL certificates are always offered at no additional cost.
03/10/2015 New chip card rule arrives in the U.S
Joining other retailers around the world, U.S. merchants now must adopt the chip-based EMV specification as their primary method of credit card acceptance – or be on the hook for fraudulent transactions. But while EMV may help reduce fraud (or at least migrate it elsewhere), it won’t end data breaches.
02/10/2015 Apple
On Sunday, September 20th, Apple said it is cleaning out malicious iPhone and iPad programs identified in the first large-scale attack on their iOS App Store. This was disclosed after numerous cyber security firms reported finding a malicious program called XcodeGhost that was embedded in hundreds of legitimate apps. It's the first reported case of large scale amounts of malicious software programs making their way through Apple's strict app review process. Before this attack, only five malicious apps had ever been found in the App Store, according to the cyber security firm Palo Alto Networks Inc.
01/10/2015 Google Disabling SSLv3 and RC4
As Google's transition to SHA-256 certificates is nearing completion, they are planning the next changes to their TLS configuration. As part of those changes, Google will be disabling support for SSLv3 and RC4 in the medium term. SSLv3 has been obsolete for more than 16 years and is so full of known problems that the IETF has decided that it must no longer be used. RC4 is a 28 year old cipher that has done remarkably well, but is now the subject of multiple attacks at security conferences.
25/09/2015 Symantec SHA-1 to be phased out
Given the increasing vulnerability of the SHA-1 Hashing Algorithm and our own SHA-1 deprecation policies, Symantec will be phasing out SHA-1 SSL certificates. This is in accordance with the CA/B Forum policy and major browsers; plans to phase out SHA-1 support via degraded visual indicators or warnings in Chrome, Firefox, and Internet Explorer. Please note: In order to mitigate issues, any SHA-1 SSL certificate expiring on or after 1 Jan 2016 needs to be replaced with a SHA-256 end-entity certificate, chained to a SHA-256 intermediate, at your customer's earliest convenience.
25/09/2015 Symantec implements CAA for all brands to prevent mis-issuance of certificates
Symantec implements CAA for all brands to prevent mis-issuance of certificates Certification Authority Authorisation (CAA) is a simple way for your customers to express their preference of CA. It is intended to reduce the risk of unintended SSL/TLS certificate mis-issuance, unintentionally or by malicious actors. The goal is to allow a DNS domain name holder to specify the certificate authority or authorities that the owner has authorized to issue SSL/TLS certificates for that domain. Symantec will check the CAA record prior to certificate issuance.
20/09/2015 New guidelines for .BANK domains
The process for issuing certificates for .BANK domains has changed. Now, When you renew or purchase an SSL Certificate for banks, bank associations, regulators and certain core service providers you may notice a little more effort and time is needed to approve the request. Symantec will verify all .BANK domains before certificate issuance; currently this process cannot be fully automated, so will take a little additional time to process. This ensures that only eligible institutions (banks, bank associations, regulators and certain core service providers) use .BANK domains.
14/09/2015 Norton Secured Seal Flash Update
As of 15th September 2015, Symantec will no longer issue Flash seal code. Gif seal and code will automatically be returned for all customer websites (which are not using customized self-hosting kits). With security best practices in mind and given the increasing vulnerability of Flash technologies, Symantec will no longer be supporting Flash for our Norton Secured Seal. There is no CA/B Forum policy to deprecate Flash for SSL/TLS certificates. However major browsers, such as Chrome, plan to disable support for Flash or already display security warnings in the browsers cautioning website visitors against Flash.
10/09/2015 Symantec
Beginning October 3, 2015, the Symantec and Veritas businesses will operate independently.
01/09/2015 Symantec
Symantec Corp. (NASDAQ: SYMC) announced that it has entered into a definitive agreement to sell its information management business, known as Veritas, to an investor group led by The Carlyle Group together with GIC, Singapore’s sovereign wealth fund, and other expected co-investors for $8 billion in cash. The transaction, which was unanimously approved by Symantec's Board of Directors, is expected to close by January 1, 2016.01/09/2015 Singapore Telecommunications Limited (Singtel) bought Trustwave
Singapore Telecommunications Limited (Singtel), Asia’s leading communications company, has completed its acquisition of Trustwave. This acquisition is a positive event for our customers, partners and employees and represents an important milestone in our company’s evolution as it strengthens Singtel’s information security capabilities and bolsters Trustwave’s ability to expand its leadership in managed security services globally.
The company will continue to operate under the industry-leading Trustwave brand – remaining headquartered in Chicago with offices worldwide – as a standalone, strategic business unit within Singtel Group Enterprise. Our mission of helping you fight cybercrime, protect data and reduce risk, remains unchanged, as we continue to operate globally, supporting our customers and partners in more than 96 countries, without reduction in our services, technology portfolio or support.
11/08/2015 Symantec Announces Sale of Veritas to The Carlyle Group
Symantec announced that it has entered into a definitive agreement to sell Veritas to a group of investors led by The Carlyle Group, a global investment firm with a strong track record of growing businesses. The transaction is expected to close at the end of the year. We believe this move offers several advantages for both Symantec and Veritas partners.
06/08/2015 SHA3 принят
Национальным институт стандартов и технологий США утвердил алгоритм хеширования SHA-3 (Keccak Кечак) в качестве федерального стандарта обработки информации , что позволяет использовать его в правительственных учреждениях США наряду с ранее стандартизированным алгоритмом SHA-2
14/07/2015 Windows Server 2003 extended support ended on July 14, 2015
Microsoft will no longer issue security updates for any version of Windows Server 2003. If you are still running Windows Server 2003 in your datacenter, you need to take steps now to plan and execute a migration strategy to protect your infrastructure. By migrating to Windows Server 2012 R2, Microsoft Azure or Office 365, you can achieve concrete benefits, including improved performance, reduced maintenance requirements, and increased agility and speed of response to the business.
13/07/2015 OpenSSL High Severity Vulnerability
Customers using the following versions of OpenSSL should patch immediately.
- 1.0.2c
- 1.0.2b
- 1.0.1n
- 1.0.1o
13/07/2015 OpenSSL High Severity Vulnerability
Administrators and developers should consider checking their servers and applications for the version of OpenSSL being used, then upgrade as required.
OpenSSL has announced a high severity vulnerability, CVE-2015-1793 which will require an upgrade to some OpenSSL installations.
The vulnerability was discovered by Google personnel Adam Langley and David Benjamin on June 24, 2015. Google has been working on an alternative to OpenSSL called BoringSSL. This has allowed Google to reduce vulnerabilities in their installations, but is also a benefit to OpenSSL as issues have been reported. Note that BoringSSL is not impacted.
OpenSSL states that “during certificate verification, OpenSSL (starting from version 1.0.1n and 1.0.2b) will attempt to find an alternative certificate chain if the first attempt to build such a chain fails. An error in the implementation of this logic can mean that an attacker could cause certain checks on untrusted certificates to be bypassed, such as the CA flag, enabling them to use a valid leaf certificate to act as a CA and “issue” an invalid certificate.” The vulnerability will impact any application that verifies certificates including SSL, TLS and DTLS clients and servers when using client authentication.
This means that an attacker can then become trusted the same as a certification authority (CA) and issue invalid publicly trusted SSL/TLS certificates for any domain. Such a vulnerability would support man-in-the-middle (MitM) attacks.
This issue impacts OpenSSL versions 1.0.2b, 1.0.2c, 1.0.1n and 1.0.1o.
- OpenSSL 1.0.2b/1.0.2c users should upgrade to 1.0.2d
- OpenSSL 1.0.1n/1.0.1o users should upgrade to 1.0.1p
10/07/2015 Symantec Important Service Announcements
We are aware and currently investigating the OpenSSL Alternative Chains Certificate Forgery Vulnerability CVE-2015-1793. This vulnerability affects OpenSSL versions 1.0.2c, 1.0.2b, 1.0.1n, and 1.0.0o and relates to OpenSSL's certificate verification process. By exploiting this vulnerability, an attacker can act as a Certificate Authority (CA) and issue invalid certificates through a valid end-user certificate.
This vulnerability does not impact you or your customers’ SSL/TLS certificates.
17/06/2015 Mozilla
В результате обсуждения проведенного среди подписчиков Mozilla, принято решение сфокусировать усилия на разработке защищенной сети HTTPS. Сервисы, связанные с незащищенной сетью HTTP будут постепенно удаляться.
12/06/2015 Wikimedia Foundation
Все сайты некоммерческой организации Wikimedia Foundation переводятся полностью на HTTPS чтобы посетители могли безопасно пользоваться сайтами компании. Весь трафик к Wikimedia сайтам будет зашифрованым.
05/06/2015 WebTrust Ukraine
Get Ranking Boost in Google with SSL Certificat >>>02/06/2015 Facebook Will Stop Supporting SHA-1 in October
As part of our commitments to helping developers build secure apps and protecting the people who use Facebook, we’re updating our encryption requirements for Facebook-connected apps to reflect a new and more secure industry standard. As a result, apps that don't support SHA-2 certificate signatures will no longer be able to connect to Facebook starting on October 1, 2015.
We'll be updating our servers to stop accepting SHA-1 based connections before this final date, on October 1, 2015. After that date, we'll require apps and sites that connect to Facebook to support the more secure SHA-2 connections.
SHA-1 SHA-2 Проверка SSL сертификата на сервере >>>
01/01/2015 Thawte
С 1 июня все Thawte SSL сертификаты имеют неограниченную лицензию на использование
21/05/2015 DigiCert Logjam Attack
Late last night, researchers announced a flaw in TLS protocol that allows a man-in-the-middle attacker to trick browsers into using export-grade cryptography and decrypt TLS communications. The attack, called Logjam, can be exploited against servers that support the Diffie-Hellman key exchange. Logjam does not affect your SSL Certificate private keys and you do not need to reissue your SSL Certificates. However, we encourage all administrators to make sure that servers are properly configured.
The attack affects any server that supports DHE_EXPORT ciphers and all modern web browsers.
* The vulnerability does not affect SSL Certificates and does not require any action related to certificate management.
14/05/2015 VENOM: уязвимость QEMU (CVE-2015-3456)
Центр безопасности Red Hat сообщает об обнаруженной уязвимости в QEMU, которая приводит к переполнению буфера эмулятора контроллера гибких дисков в QEMU. Это подвергает риску безопасность систем с гипервизорами KVM/QEMU и Xen. Уязвимость получила кодовое название «VENOM», ей был присвоен рейтинг на уровне ВАЖНО и назначен код CVE-2015-3456. QEMU — система эмуляции и виртуализации аппаратного обеспечения компьютера с открытым исходным кодом, которая интегрируется в некоторые решения Red Hat для эмуляции оборудования виртуальных машин, работающих под управлением Xen и KVM/QEMU. Привилегированный пользователь виртуальной машины потенциально может вызвать ее сбой и запустить произвольный код в хост-системе с разрешениями QEMU. Даже если виртуальный дисковод не настроен, эту уязвимость все равно можно будет эксплуатировать. Проблема кроется в контроллере гибких дисков, инициализируемом для каждого гостя x86 и x86-64 независимо от его конфигурации — и его невозможно отключить или удалить. В настоящее время негативных последствий можно избежать, запретив недоверенным пользователям виртуальных машин получать разрешения уровня администратора. Все программные решения Red Hat, в рамках которых предоставляется QEMU, попадают в группу риска
14/05/2015 Mozilla Deprecating Non-Secure HTTP
Today we are announcing our intent to phase out non-secure HTTP. There’s pretty broad agreement that HTTPS is the way forward for the web. In recent months, there have been statements from IETF, IAB (even the other IAB), W3C, and the US Government calling for universal use of encryption by Internet applications, which in the case of the web means HTTPS. After a robust discussion on our community mailing list, Mozilla is committing to focus new development efforts on the secure web, and start removing capabilities from the non-secure web. There are two broad elements of this plan:
- Setting a date after which all new features will be available only to secure websites
- Gradually phasing out access to browser features for non-secure websites, especially features that pose risks to users’ security and privacy.
14/05/2015 Google
Since 2008 we’ve been working to make sure all of our services use strong HTTPS encryption by default. That means people using products like Search, Gmail, YouTube, and Drive will automatically have an encrypted connection to Google.
This year, we’re working to bring this >“HTTPS Everywhere” mission to our ads products as well, to support all of our advertiser and publisher partners.
We’ve moved all YouTube ads to HTTPS as of the end of 2014.
Search on Google.com is already encrypted for a vast majority of users and we are working towards encrypting search ads across our systems.
By June 30, 2015, the vast majority of mobile, video, and desktop display ads served to the Google Display Network, AdMob, and DoubleClick publishers will be encrypted.
Also by June 30, 2015, advertisers using any of our buying platforms, including AdWords and DoubleClick, will be able to serve HTTPS-encrypted display ads to all HTTPS-enabled inventory.
14/05/2015 Quarterly SSL Industry Snapshot
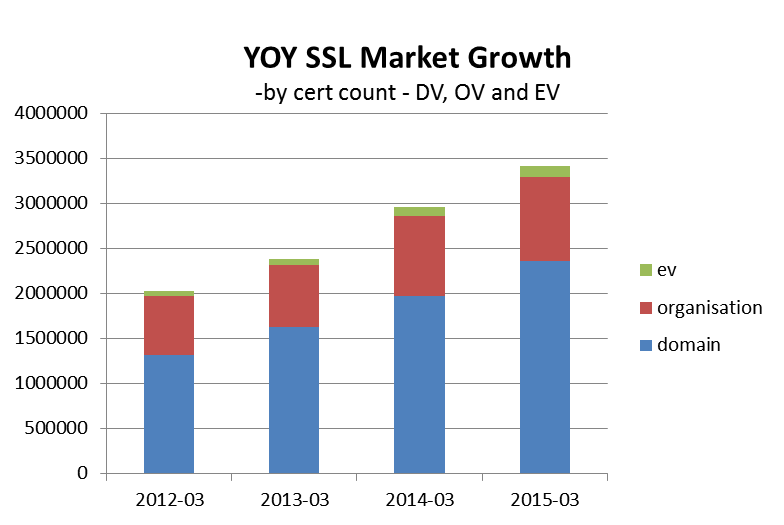
- March 2015 the total SSL market grew 13% compared to March 2013
- Q4 2014 shown a 4% growth in total SSL units over Q3 2014
- Total EV units grew by 15% in March 2014 over March 2014
- Total OV units grew by 5% in March 2014 over March 2014
- Total DV units grew by 16% in March 2015 over March 2014
14/05/2015 Think Twice Before Using Domain Validated SSL Certificates for E-Commerce
Make sure are aware that a Domain Validated (DV) certificate should not be used for E-Commerce. See the "Hidden Dangers Lurking in E-Commerce." white paper
13/05/2015 Symantec Highlights from the 2015 Internet Security Threat Report
Knowing how cybercriminals are threatening security is the first step to securing your information—and your company’s goals. From social media vulnerabilities to digital extortion, the 2015 Symantec Internet Security Threat Report leverages an unparalleled amount of data and is the resource you need to quickly uncover digital threats.
Key Findings:
- How cyberattackers leap-frog corporate defenses
- Why ransomware attacks soared 113% in 2014
- How social networks and apps enable cybercriminals
- Why corporate defenses are falling behind as cybercriminals move faster
- Why attacks on Internet of Things devices are more serious than ever
12/05/2015 Symantec Norton Identity Safe
Norton Identity Safe - бесплатный менеджер паролей, который делает вход на постоянно посещаемые вами веб-сайты быстрым, удобным и безопасным. Простой менеджер паролей для вашего веб-браузера, Android-смартфона, iPhone и iPad
08/05/2015 Fast Facts on DDoS Attacks
Neustar conducted research with hundreds of IT professionals like you to identify the latest trends in DDoS attacks and the techniques being used to minimize their impact. As a leader in DDoS protection and mitigation, Neustar offers solutions that fit your security requirements including cloud-based, on-premise and hybrid services. Backed by a 24/7 Security Operations Center, a carrier-grade infrastructure, best-in-class technologies and staff with unparalleled experience and expertise, Neustar can help your organziation have a brighter future against DDoS. It's not a pretty picture. to quickly learn how evolving DDoS threats can hurt you Full Neustar Annual DDoS Attacks and Impact Report is here
05/05/2015 PCI Security Standards Council
On Feb. 13, the PCI Security Standards Council informed its assessor community that SSL (Secure Sockets Layer) – a protocol designed to ensure that data provided between a web server and a web browser, such as credit card information, remains secure – is no longer an acceptable way to provide "strong cryptography." In March, the council made the news official by offering additional information in the form of an FAQ , including encouraging merchants to upgrade to SSL’s successor, a much-stronger protocol known as Transport Layer Security (TLS). The PCI council also stated that later this month it will publish an update (version 3.1) to the PCI DSS. An update to the Payment Application DSS (PA-DSS) is scheduled to follow. Merchants will be given a certain amount of time to implement the changes. While the council doesn’t plan to immediately crack the whip on retailers, many of whom are still getting comfortable with the 3.0 versions of both payment standards, businesses should become familiar with their new payment security responsibilities.
03/05/2015 SSL Certificates without localhosts and IP addresses
Due to introducing by CA/Browser Forum (CA/B) its guidelines, issuing of SSL certificates for IP addresses and server internal names won’t be allowed if its validity period exceed November 1st, 2015. and the October 1st, 2015 as the deadline for revocation of all certificates containing an IP address or internal name as the SAN (Subject Alternative Name) or CN (Common Name) .
What does it mean?
If you are running a server that is using a local names or IP address, you should change it to a public domain (based on gTLD or ccTLD) or change your certificate to one that meets the above date. All internal connections that require a public certificate must be made using names that are verifiable.
Check if above changes affect your certificate If the values of "Website" or "Alternative names (SANs)" fields is inconsistent with the CA / Browser guidelines, a certificate will soon be unrecognized.
24/04/2015 Thawte SGC SuperCerts
С 1 июля мы прекращаем выпуск Thawte SGC SuperCerts
* Ранее выпущенные сертификаты Thawte SGC SuperCerts продолжат свою работу до истечения срока
22/04/2015 Neustar. DDOS ATTACKS AND PROTECTION REPORT
Industry survey reveals trends in DDoS threats — and how enterprises are defending themselves.
- How attacks are changing — last year 90% of business were hit more than once;
- The tools businesses are using to protect against DDoS attacks;
- The other cybercrimes that victimize companies during DDoS attacks.
- How much attacks cost — and what your business can learn from recent DDoS attacks in financial services, technology and retail 70% компаний вкладывают больше в профилактике, чем в прошлом году. Даже небольшие атаки может иметь огромное финансовое влияние
- 52% компаний испытывают кражи данных о клиентах, интеллектуальной собственности или средств, во время нападения
Все больше компаний внедряют гибридные обороны подходы. Neustar опрошенных сотни ИТ-специалистов в Великобритании (и в других странах ЕС), чтобы получить широкую перспективу на текущем угрозы и влияние на бизнес DDoS атак на своих предприятиях. Доклад ...>>> показывает некоторые удивительные тенденции в атаках на протяжении последнего года:
22/04/2015 Symantec. DV cert problem
“Doing any type of ecommerce transaction on a DV-only site poses risk”
Online criminals are exploiting a weakness in web encryption certificates to prey on consumers’ trust in the system, warns from Symantec.
Cyber-fraudsters are no longer just copying the look of a legitimate site — they’re now configuring the fakes for the modern mark of online trust: A padlock icon in the browser bar.
"Consumers have been trained to look for the padlock" in their browser before giving up any sensitive information, such as payment card data or passwords, writes author Dean Coclin in a blog post Symantec will put up later today.
The lock icon is put there by digital certificates, which encrypt Internet traffic between browsers and websites — assuring consumers they are securely connected to the genuine site. But not all digital certificates are created equally.
The weakest and cheapest type of certificate, known as Domain Validation, requires nothing more of website owners beyond proving that they control the web address. So the fraudsters who recently registered paypol-france.com (an obvious rip off of PayPal) were able to purchase a legitimate web certificate within minutes of registering it, meaning consumers visiting the site would have seen a padlock.
Certificate authorities, the organizations that issue certificates, perform an automated “fraud check” meant to weed out obvious bad sites — but the algorithm isn’t perfect. And even when it works, that doesn’t prevent cyber criminals from grafting bank names onto innocuous-sounding but malicious sites, such as the thieves who created https://url-bofa.support/BankOfAmerica.Com.
16/04/2015 Symantec OCSP
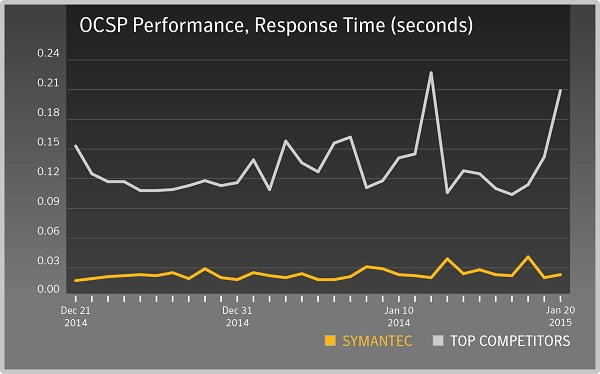
OCSP (Online Certificate Status Protocol) is a newer way to validate the revocation status of X.509 digital certificates. OCSP has superseded the previous protocol CRL (Certificate Revocation List) and improves upon some of its shortcomings.
A major limitation of CRL checking is that updates need to be frequently downloaded in order to maintain a current list of valid X.509 certificates on the client end. This in turn can put a burden on the client’s network and calling resources. OCSP responses contain less information than CRL checking, which in turn decreases the burden on the client network.
Symantec further improved OCSP performance by building a highly efficient and responsive OCSP infrastructure to ensure X.509 validity can be checked quickly and with minimal effort from the client. The result is that Symantec is the fastest in the industry in determining X.509 digital certificate status.
Notice on Legacy VeriSign URLs
Starting in July the transition from VeriSign to Symantec URLs will be complete. Partners will be automatically redirected to the new Symantec URLs. This will impact all URLs, except those essential for the functioning of active certificates. You will be redirected to the Symantec URLs when you go to the VeriSign URLs. Please be sure to update your bookmarks and any localized/customized content to reflect the updated URLs prior to August 10, 2015.
08/04/2015 Trustwave
Trustwave today announced a new strategic investor that will bolster our ability to expand, grow and continue delivering industry-leading managed security services and technologies that help you fight cybercrime, protect data and reduce security risk.
Singapore Telecommunications (Singtel) has signed a definitive agreement to acquire Trustwave and become our new majority investor. The agreement is effective immediately but subject to satisfactory completion of customary regulatory requirements. Singtel is Asia’s leading communications group with a presence in 25 countries. It is publicly traded on the Singapore Exchange.
Joining Singtel will give us the ability to leverage its global presence and resources and accelerate worldwide adoption of our industry-leading security solutions. Singtel is the perfect partner for us as we continue to expand and grow our business, and we’re thrilled to become a part of such a prestigious and innovative organization.
Following the close of the acquisition, Trustwave will operate as a standalone business unit – albeit with increased resources and capabilities from Singtel – with continued enhancement of the services, products and support we provide you. Trustwave will continue to operate globally under the Trustwave brand without reduction in our services, technology portfolio or support.
02/04/2015 Thawte SGC SuperCerts Have Been Discontinued
The Thawte SGC SuperCert has been discontinued by the vendor. Effective immediately, per the direction of Thawte,
we have ceased all new orders of the Thawte SGC SuperCert. SGC has become almost entirely obsolete, so for most situations it is no longer needed.
Note: If you currently have an existing Thawte SGC SuperCert that has been issued, the certificate will continue to secure your website
until the expiration date of the certificate.
25/03/2015 Symantec New OpenSSL Vulnerability Could Facilitate DoS Attacks
After days of speculation, OpenSSL has finally released patches today for a slew of previously unknown vulnerabilities in OpenSSL including one rated as high severity. Given the high severity rating, the announcement will likely cause a scramble among systems administrators to update vulnerable installations before attackers begin to exploit the flaw.
25/03/2015 Symantec Maximum Validity for OV/DV SSL Certificates
Effective April 1st, 2015, and in accordance with industry-wide policy intended to increase SSL/TLS security, the replacement of existing SSL certificates will be limited to a maximum period of 39 months. For QuickSSL, QuickSSL Premium, RapidSSL, and RapidSSL Wildcard certificate replacements, users can utilize the full term of the original certificate as long as they come in for a second replacement approximately one year later. No refunds will be provided for these products. For all other products, Symantec will process partial reimbursements
25/03/2015 Symantec New FREAK Vulnerability
A new SSL/TLS vulnerability named “FREAK” was identified by several security researchers. It’s a threat because FREAK allows an attacker to get between a client and server and view what is intended to be a secure and private communication. The vulnerability is primarily due to a bug in OpenSSL client software, but only exploitable on poorly-configured web servers. Both clients and servers are at risk. Web site owners can protect their sites by properly configuring their web servers. End users will need to wait for browser vendors to release new versions that include the OpenSSL bug fix.
* Note that this vulnerability is not related to SSL certificates. Existing certificates will continue to work as intended; no certificate replacement is needed.
18/03/2015 The Hacker News
The OpenSSL Foundation is set to release a handful of patches for undisclosed security vulnerabilities in its widely used open source software later this week, including one that has been rated "high" severity.
In a note published last night, Matt Caswell of the OpenSSL Project Team announced that OpenSSL versions 1.0.2a, 1.0.1m, 1.0.0r, and 0.9.8zf will be released Thursday.
"These releases will be made available on 19th March," Caswell wrote. "They will fix a number of security defects. The highest severity defect fixed by these releases is classified as "high" severity."
OpenSSL is an open-source implementation of the SSL and TLS protocols. It's a technology that's widely used by almost every websites to encrypt web sessions, even the Apache web server that powers almost half of the websites over the Internet utilizes OpenSSL.
13/03/2015 Symantec
Symantec FAQ при перевыпуске текущих >DV и OV сертификатов срок действия которых составляет 4,5 или6 лет >>>
* согласно CA/Browser Baseline Requirements
12/03/2015 TrustWave
- • Pressure is on: 54% of security pros felt more pressure to secure their organizations in 2014, and 57% of respondents expect to experience additional pressure to secure their organization in 2015.
- • Differing perspectives: 64% of enterprise respondents foresee increasing pressure in 2015, compared to 48% at SMBs.
- • False sense of security: 70% of overall respondents said they are safe from cyberattacks and data compromises.
- • Jumping the gun: 77% of respondents were pressured to unveil IT projects that weren’t security ready.
- • Breaking in: 62% of respondents were most pressured by external threats, versus ones stemming internally.
- • Reaching out for help: 78% of respondents said they are likely or plan to partner with a Managed Security Services Provider (MSSP) in the future.
- • “Emerging” concern: Adoption of emerging technologies, such as the cloud and BYOD, overtook advanced security threats as the top operational pressure facing respondents.
- • Cloudy forecast: Among emerging technologies, 47% of security pros were most pressured to use or deploy the cloud, up from 25% the previous year.
- • Corner-office commands: 61% of respondents felt the most “people pressure” was exerted by their owners, board and C-level executives — up from 50% the previous year.
- • Password disconnect: 9% of security pros cited weak passwords as the insider activity they felt most pressure to fend off, despite previous Trustwave research showing easy-to-crack passwords contributed to nearly one-third of all breaches.
- • Send in the reserves: 84% of respondents said they wanted the size of their IT security team increased.
- • Fallout phobia: 84% of respondents cited reputation or financial damage as their biggest fear if their organization is breached.
11/03/2015 GlobalSign
GlobalSign invites you to join us on this Webinar to learn how your organization can utilize SharePoint roles to the fullest extent and enable external users to manage their own identities and preferred authentication methods through advanced technologies such as user-driven federation.
We will also share three uses cases that highlight how each organization is managing external users and access to their SharePoint extranet portals to provide a better and more secure user experience.
Additionally, we’ll show you just how quickly and cost-effectively you can deploy an Identity Relationship and Access Management (IRAM) solution that meets your SharePoint requirements.
- Provide one identity across multiple SharePoint sites with single sign-on (SSO)
- Protect sites properly with appropriate authentication and authorization through delivery of SharePoint claims (roles)
- Bring together business ecosystems to access SharePoint with users’ own credentials
- Add strong authentication or social log-in to SharePoint
- Translate SharePoint roles of external identities to business oriented roles with self-service, workflows and mandates
05/03/2015 Changing Symantec OV & DV Certificate OIDs
Starting March 5, 2015, we will change all OV and DV certificate policy OIDs to the CAB Forum certificate policy OIDs. This will help relying parties differentiate between OV and DV certificates.
- Current Policy OID:
DV and OV: 2.16.840.1.113733.1.7.54 - CABF OIDs:
DV: 2.23.140.1.2.1
OV: 2.23.140.1.2.2
* Note: GeoTrust DV policy OIDs will change in the upcoming months.
05/03/2015 Symantec Online Verification for OV SSL Orders
With this method, we still require a verified third party telephone number for the organization and for the organizational contact to be a full time employee of the organization. If we are not able to speak to the contact when we call the verified number, we will try to confirm the contact’s email address with the operator. This will determine where we may leave the Verification Code. We send the Verification email to the contact. Once the contact views the email, they will only need to click on the link provided in the email, enter the correct code (which may be left via voicemail or email), check the confirmation box, and click Submit. With those few simple steps, the verification step is completed. There is no need for the contact to confirm the order details verbally.
06/03/2015 Symantec enroll for www.domain.com and Get domain.com as a Free SAN and when the common name is *.domain.com - add domain.com for free.
Products benefiting from this change:
| Symantec | Thawte | GeoTrust** |
| Secure Site Pro with EV | SSL Web Server with EV | True BusinessID with EV |
| Secure Site with EV | SGC SuperCerts | True BusinessID Wildcard |
| Secure Site Pro | SSL Web Server Wildcard | True BusinessID |
| Secure Site Wildcard | SSL Web Server | |
| Secure Site | SSL123 (DV, but included) |
*Qualifying common names begin with “www.” and do not contain sub-domains. E.g. www.subdomain.domain.com would not qualify for the free SAN.
Note: To take advantage of this enhancement, do not include the free SAN in your SSL certificate enrollment – Symantec’s systems will automatically add the free SAN for you.
**GeoTrust already offers domain.com as a free SAN when the common name is www.domain.com, but will now also add www.domain.com as a free SAN when the common name is domain.com.
20/02/2015 Symantec
С 1 марта 2015 года согласно Правилам SSL Symantec (Thawte, GeoTrust) прекращает выпуск сертификатов SSL на срок 4 и 5 лет.
11/02/2015 Quarterly SSL Industry Snapshot
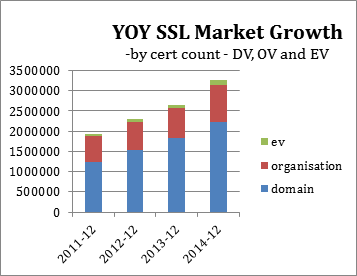
- December 2014 the total SSL market grew 23% compared to December 2013
- Q4 2014 shown a 4% growth in total SSL units over Q3 2014
- Total EV units grew by 5% in Q4 over Q3 2014
- Total OV units grew by 2% in Q4 over Q3 2014
- Total DV units grew by 5% in Q4 over Q3 2014
11/02/2015 Symantec Expands Availability Of Ready Issuance Feature
Symantec is excited to announce its plan to roll out the Ready Issuance feature globally. Ready Issuance is a new authentication feature where a customer can go through the authentication once so they can instantly issue more certificates for their environment.
11/02/2015 Announcing Veritas, The Information Management Brand
We are pleased to introduce Veritas Technologies Corporation – the new name of the independent information management business that will be created following the completion of the previously announced separation of Symantec into two companies later this year.
06/02/2015 Unlimited licenses for all our Thawte SSL certificates
 The license policy for our Thawte brand is changing to offer unlimited licenses for all our Thawte SSL certificates.
The change will be implemented by 20th February 2015 for our partners and by March 5th 2015 for our direct customers.
The license policy for our Thawte brand is changing to offer unlimited licenses for all our Thawte SSL certificates.
The change will be implemented by 20th February 2015 for our partners and by March 5th 2015 for our direct customers.
01/02/2015 С 3 февраля 2015 года. Symantec прекращает выпуск и отзывает существующие SSL и CodeSign сертификаты для Крыма
Отозваный сертификат This is to inform you that Symantec has the obligation to comply with the Executive Order 13685 issued by President Obama on December 19, 2014. This executive order prohibits new investment by US persons in Crimea; exports of goods, technology or services to Crimea. As a result of this Symantec will cancel all active orders and services for end users located in the Crimea region >>>.
27/01/2015 1 марта 2015 года SSL Symantec прекращает выпуск сертификатов SSL на срок 4 и 5 лет.
This is in accordance with new guidelines set forth by the Certificate Authority/Browser (CA/B) Forum, the governing body of the SSL industry. This update will affect all SSL certificates in the industry, including the entire product catalogs of Symantec, Thawte, GeoTrust, and RapidSSL. (EV certificates are already limited to a maximum of two years so they are not affected by this change).
Please note that any active 4 or 5 year certificate that are reissued after the March 1st, 2015 deadline will automatically be truncated to the new maximum duration permissible, which is 39 months. Any active 4 or 5 year certificate that is reissued before this deadline will be unaffected. Therefore, adgrafics strongly recommends that any new SSL purchase be for no more than a maximum of 3 years, in order to avoid any lost time and money due to a reissue.
All 4 or 5 year certificates reissued after the March 1st deadline will be truncated to the new maximum industry standard of 39 months.
Ultimately, this is good news for the SSL industry, as certificates with shorter lifespans make security updates much easier and more streamlined. So, recent updates like the SHA-2 upgrade, internal domain issuance, and more industry-wide enhancements that have become quite commonplace with SSL will be much less of a hassle.
Also, certificates with shorter lifespans will offer more in the way of security, as companies will have to reaffirm their identities in a more timely fashion. It goes without saying that trust and security are of paramount importance to the SSL market, so any effort to enhance either of these components is good for the overall health of the market.
21/01/2015 Google Chrome To Begin Marking HTTP as Insecure
Google Chrome has long been a leader in internet security, and a very active member of the Certificate Authority/Browser (CA/B) Forum – the self-governed SSL regulations organization. One of their most recent announcements is their intention to start actively marking HTTP as insecure, placing an even higher level of importance on SSL certificates.
As we all know, SSL certificates enable the use of the HTTPs (HTTP Secure) protocol. Without SSL, browsers connect with HTTP, which does not have any encryption or authentication capabilities. Currently, browsers show the well-known green padlock and/or green address bar (with an EV certificate) when a site is using SSL along with HTTPs, but don't show any indication of a lack of security for a site that is NOT using SSL. Google Chrome's Security Team does not think this is quite right.
They have a multi-stage plan that includes actively marking non-secure origins and alerting users of a lack of SSL protection. Combined with their announcement a few months back that sites with SSL will get preferential treatment when it comes to SEO rankings, this recent Google update about actively marking sites as "insecure" without a certificate places an even higher emphasis for website owners to equip their site with SSL certificate.
After making their original announcement in mid-December1, they have quickly followed up with an experimental feature added to Chrome in the first week of January.2
All indications are that this plan will not be taking full effect for quite some time; however, it certainly represents a major change in thought. It is especially encouraging to see a push for more transparent, apparent, and honest security notifications from a company as large as Google. Large campaigns from global companies such as Google have the ability to bring awareness to large swaths of internet users.
07/01/2015 2015 – Looking Back, Moving Forward
End of 1024-Bit Security
In 2014, the SSL industry moved to issuing a minimum security of 2048-bit RSA certificates. Keys smaller than 2048 are no longer allowed in server certificates. In addition, Microsoft and Mozilla started to remove 1024-bit roots from their certificate stores. Hopefully, the key size change will support users through to 2030.
Push to Perfect Forward Secrecy
Following the Edward Snowden revelations of pervasive surveillance, there was a big push to configure web servers to support Perfect Forward Secrecy. For the most part, this is a reconfiguration of the ciphers to prefer those that support Diffie-Hellman Ephemeral (DHE). With perfect forward secrecy, a compromise of the server private key will not allow secured communications to be decrypted.
TLS Stack Issues
In 2014, issues were found with all TLS stacks and created some new stack versions.
Apple had the Goto Fail bug where the certificate was not authenticated which could lead to a man-in-the-middle (MITM) attack.
GnuTLS, used in products such as Red Hat desktop/server and Debian and Ubuntu Linux distributions, also had an issue with improperly verifying digital certificates as authentic. The vulnerability allows an attacker to impersonate a trusted site and create a certificate that would be accepted by a user.
OpenSSL followed up with a security issue coined Heartbleed. With Heartbleed, an attacker could read the memory of the web server which may reveal the private key or end user passwords or data. XKCD depicted the issue quite nicely.
NSS crypto library had the BERserk bug ,which impacted Mozilla products such as Firefox and Google Chrome. This vulnerability allows for attackers to forge RSA signatures and bypass authentication to SSL protected websites. Users on a compromised network could reveal passwords or download malware.
Microsoft completed the set with revealing a bug to Schannel later dubbed WinShock. This vulnerability grants code execution where an application such as Internet Explorer may be triggered by a component outside the protected environment. In the case of client targeted attack, it is easy to achieve control during normal browser exploitation which raises its severity.
The good news is that OpenBSD and Google are trying to raise the security of the TLS stacks by preparing their own versions. OpenBSD developed LibreSSL which is a cut-down version of OpenSSL. OpenBSD has tried to simplify by eliminating old code which supports legacy platforms.
Google also announced its version of OpenSSL called BoringSSL. Google is striving to keep SSL boring by deploying HTTPS without bugs.
Google SHA-1 Deprecation
Google advanced the schedule of SHA-1 deprecation. The industry was already working to the policy implemented by Microsoft where the certification authorities (CAs) would stop signing with SHA-1 in 2016 and Windows would stop supporting SHA-1 in 2017. Google supports the policy, but has also decided to provide warning indicators in Chrome as early as 2014 for SHA-1 signed certificates which will expire in 2016 or later. As a result, the CAs advanced communications to certificate customers to accelerate the migration to SHA-2.
POODLE
Google also announced the POODLE vulnerability. With POODLE, an attacker can downgrade the SSL/TLS session to SSL 3.0. Once SSL 3.0 has been agreed, then through a padding oracle attack, it will allow items such as “secure” HTTP cookies or HTTP authorization header contents to be stolen. The result was the ability to use SSL 3.0 was removed from many servers and browsers. In addition, some servers were patched to prevent the fallback to SSL 3.0.
It was later revealed POODLE could also be used against the TLS versions of the protocol. In this case, padding was performed incorrectly in about 10 percent of the web servers. The impacted server vendors then had to release patches to mitigate POODLE.
To 2015 and Beyond
Early in 2014, Google announced Chrome would start supporting CT for EV SSL certificates in 2015. As a result, the CAs advanced their schedules and have implemented CT for all new EV SSL certificates. To support existing EV certificates, the CAs have provided these to Google which will be whitelisted for Chrome. As such, all EV certificates should be publicly logged in 2015. The public logging will allow monitoring to be developed. Monitoring will provide domain owners the chance to see when an EV certificate has been issued with their domain. Moving forward we will see CT progressed through the IETF and a new RFC released sometime in the future. We may also see CT extended to support DV and OV SSL certificates. Certification Authority Authorization (CAA) The CA/Browser Forum has implemented a change to the SSL Baseline Requirements to require all CAs to disclose their policy on CAA by April 2015. Implementation of CAA will allow domain owners to specify their CA through DNS or DNSSec. Code Signing Baseline Requirements The CA/Browser Forum has advanced the development of the Code Signing Baseline Requirements. The draft requirements were provided for public review in the fall of 2014. The requirements will be updated and submitted for approval in 2015. The baseline requirements will provide direction to mitigate threats, such as private key protection, identity verification and threat detection. Certificate Validity Limited to 39 Months As of April 1, 2015, the maximum validity period of non-EV SSL certificates will be limited to 39 months as specified in the CA/Browser Forum SSL Baseline Requirements. The Baseline Requirements do allow for some exceptions where 60 month certificates can be issued. The reduction of validity periods will allow certificates with old requirements to expire on a timelier basis which will promote the web server to be upgraded with certificates that meet the latest requirements. Stop Using Non-Registered Domains As per the SSL Baseline Requirements, public trusted certificates with non-registered domain names will no longer be issued as of November 1, 2015. Any certificates with non-registered domain names that are still valid must be revoked by October 1, 2016. Subscribers using these certificates are encouraged to change their systems to support registered domain names. If this is not possible, then consider using a dedicated CA or a service from a CA vendor with private trust. More information can be found in the CA Security Council whitepaper. TLS 1.3 With the POODLE elimination of SSL 3.0 and the vulnerabilities of TLS 1.0 and 1.1, the best implementation of the SSL/TLS protocol is TLS 1.2. So what’s next? TLS 1.3 is on the horizon. Hopefully in 2015 we will see the release of TLS 1.3 which will allow browser and server vendors to implement. We will also want to push for TLS 1.3 deployment in order to mitigate an attack against TLS 1.2.
